Cisco Firepower Malware and File Policy, as the name suggests, gives the capability to inspect and control the files as they are transmitted over the network. We can inspect them with local or cloud anti-malware (AMP) to detect and block malware files. We can also control files based on file types if they are allowed to be transmitted over the network.
Cisco Firepower Malware and File Policy
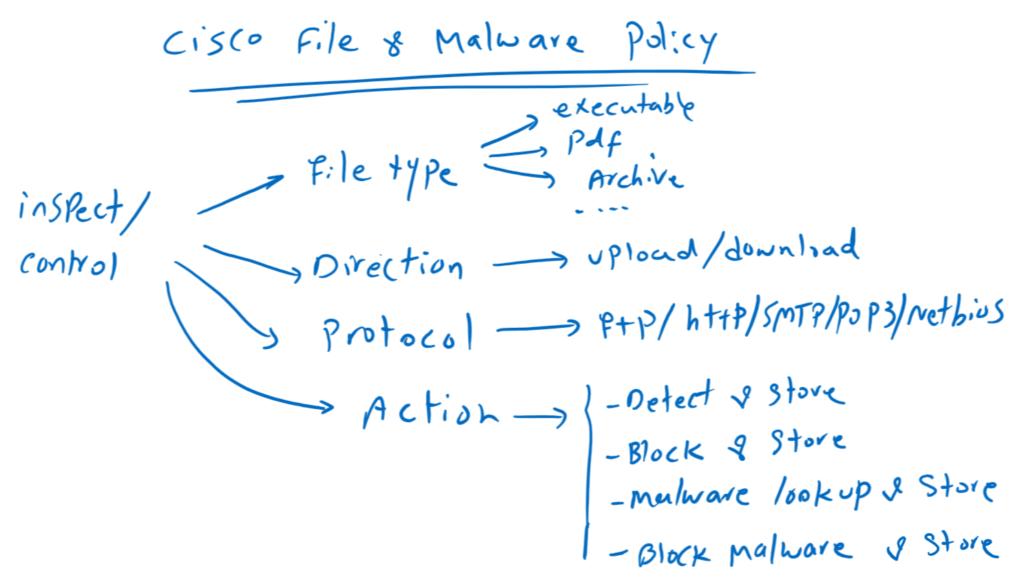
As you can see in the image, Cisco FTD Malware and File Policy allows files to be inspected during transfer based on file type, direction, and protocol.
About 60 file types can be detected by Cisco FTD when they are downloaded or uploaded during many protocols including http, ftp, email and NetBIOS. File transfer over https can also be inspected if we implement SSL decryption policy.
There are four main actions that we can apply to each rule in Malware and File policy.
Detect Files: log the detection of specific file types, while allowing transmission.
Block Files: block specific file types. There is option to reset the connection when a file transfer is blocked, and store captured files to the device.
Malware Cloud Lookup: Query the file with cloud and local malware analysis and log whether the file is malware, clean or unknown.
For cloud malware analysis, we have two options:
- Spero Analysis – Firepower examines metadata and header information of executable files and generate a signature. Then the signature of executable files are submitted to the AMP cloud.
- Dynamic Analysis – Sends files to AMP Threat Grid for further inspection.
Block Malware: Calculate the SHA-256 hash of specific file types, query the AMP cloud to block if the file contains malware.
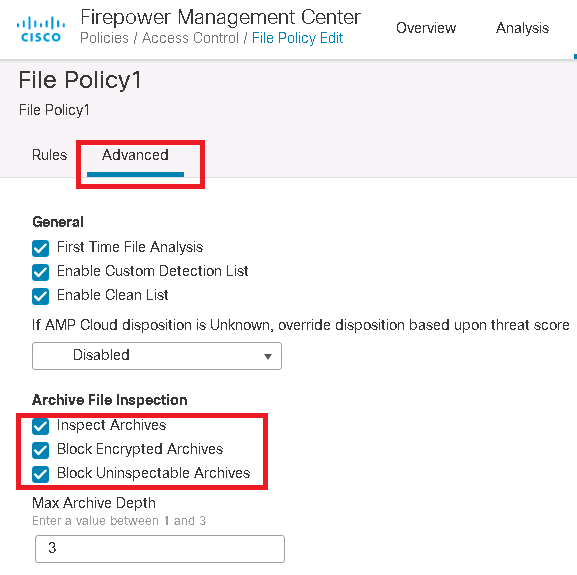
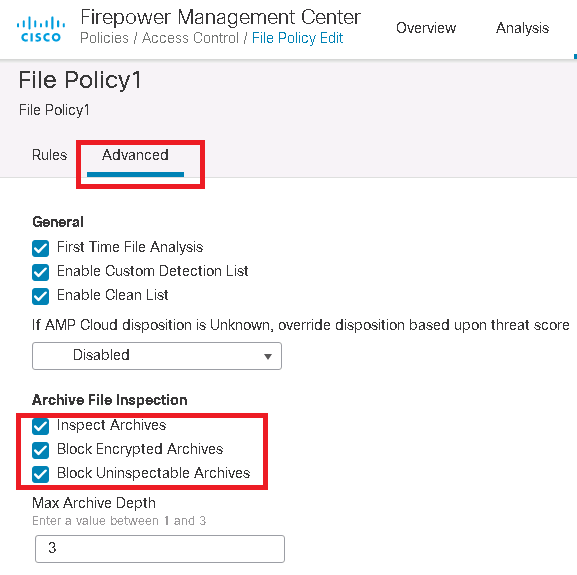
In advance section of malware and file policy, we have the option to enable inspection of archive files and also block encrypted and uninspectable archive files.
a few points regarding malware and file policy
There are a few points about malware and file policy that aren’t bad to explain.
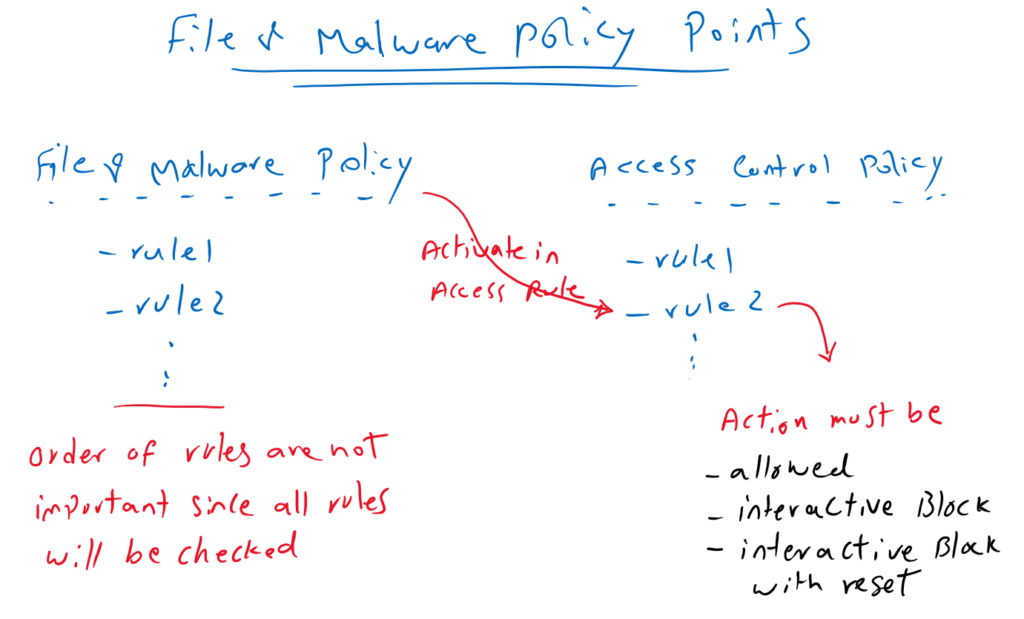
In malware and file policy, unlike access control policy, the order of the rules are not important because files are checked with all rules configured in malware and file policy and actions related to all rules will be applied to the files.
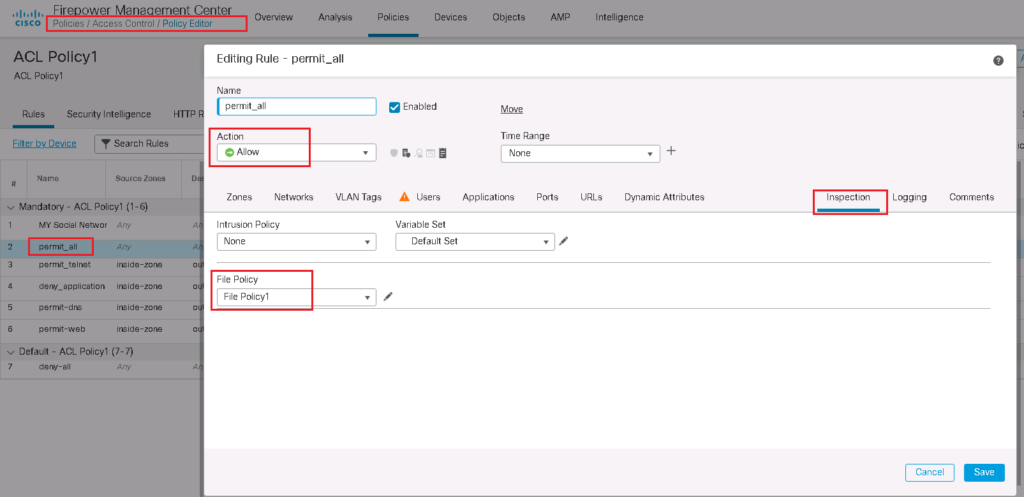
To use the malware and file policy, it must be enabled in the access control rule. It is important to note that you cannot apply malware and file policy in access control rules with blocking action since the file is blocked and it makes no sense to be checked with malware and file policy.
In other words, malware and file policy can only be configured in access control rules whose action is “allow“, “interactive block“, or “interactive block with reset“.
Cisco Firepower Malware and File Policy Configuration
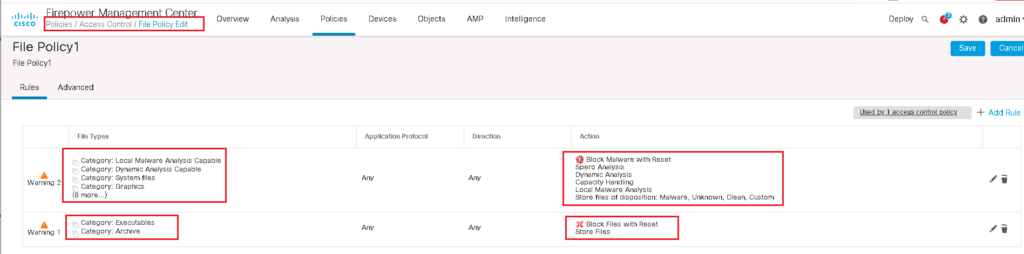
To implement just one example, we block all executable files and archive files which are transmitted over the network. We also check all file types to be examined by local and cloud malware analysis and block the file if they are malware.
Malware and File Policy Example
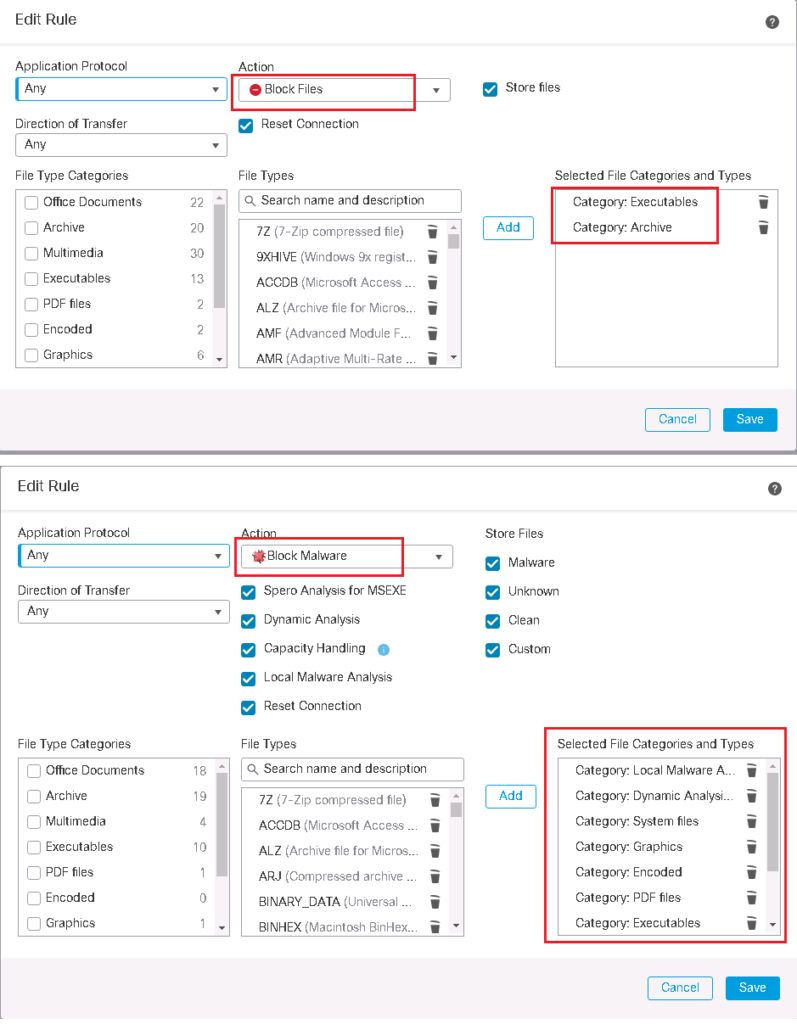
in advance tab, we configure so that archive files to be inspected and encrypted and uninspectable archive files to be blocked.
Now malware and file policies need to be enabled in the access control policy rule. As I said earlier, the access rule action should preferably be “Allow”. then it makes sense to inspect the files according to the file policy.
File Policy Test
Now we can test configured malware and file policy by downloading some files via HTTP protocol. Files transferred over https can be also inspected with the condition that SSL inspection policy is already configured.
# download sample files of different types
http://www.lancsngfl.ac.uk/cmsmanual/index.php?category_id=14
#TEKDEFENSE MALWARE SAMPLES
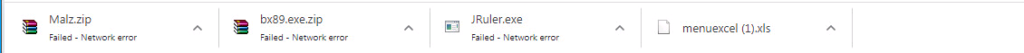
as you can see we are not allowed to download executable (.exe) and archive (.zip) files.
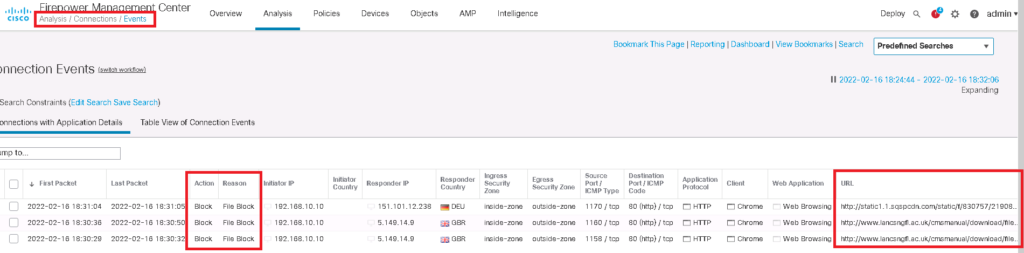
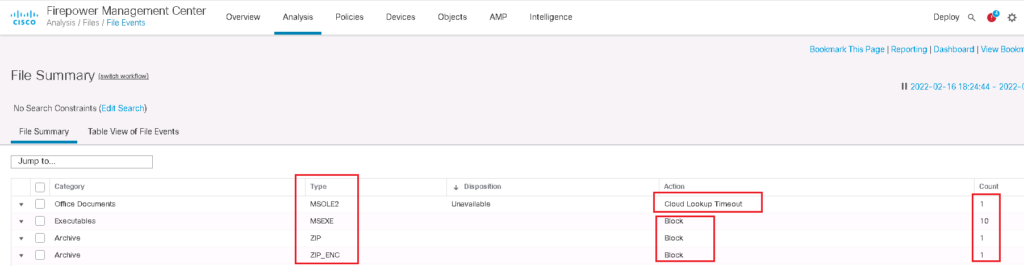
In connection events, we can see that the files are blocked but details like file name and file type are not shown.
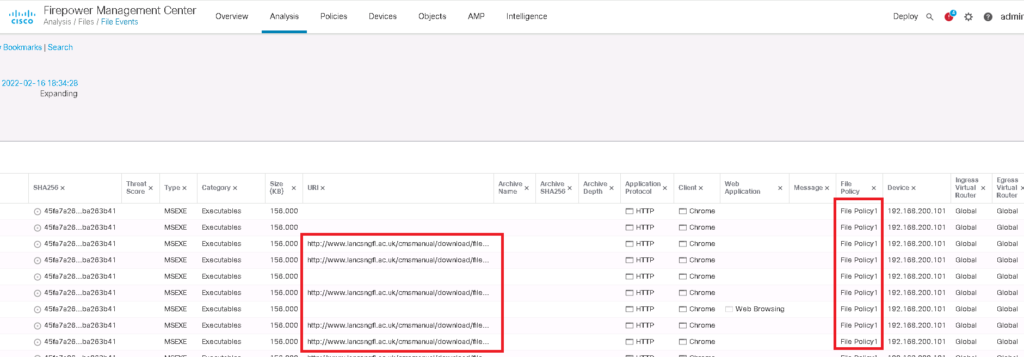
So we check “File Events” instead of “Connection Events”, in which the detail, including file type, file name and the number of counts are logged.
In table view of file events, you can make sure that the files are matched with the configured malware and file policy.
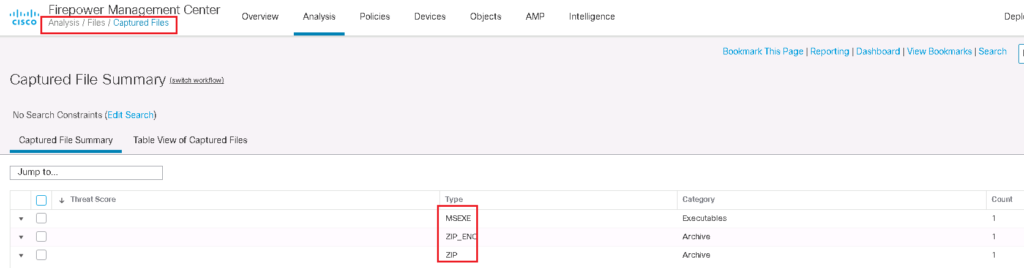
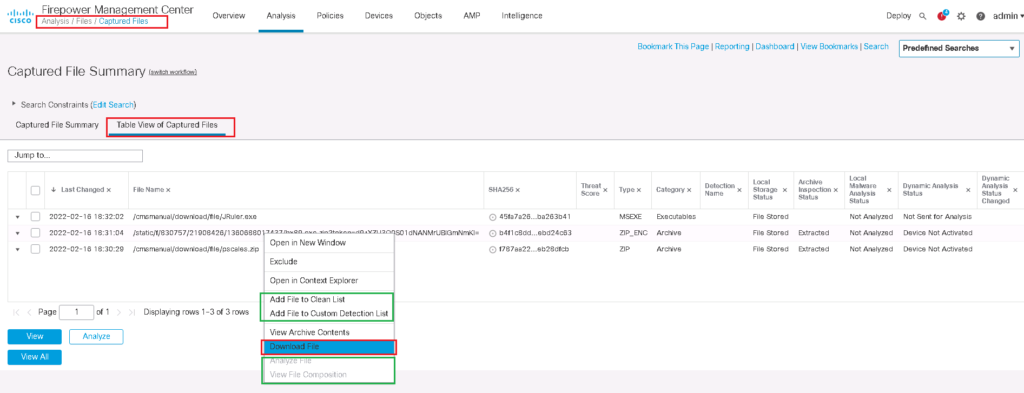
If you remember, in our policy we have also configured to store the files which are blocked. In “Analysis -> Files -> Captured Files”, you can also check the files which are stored in FMC for downloading and further analysis.
Malware Policy Test
As a sample I want to also download a virus file to check the reaction of FTD malware detection.
# download http test virus files
http://www.csm-testcenter.org/test?do=show&subdo=antimalware&test=content_types
as my expectations, malware is detected in FTD and virus samples are blocked.
You can check the reaction in “Analysis -> Files -> Malware Events”.