Cisco FTD NAT is the most basic and important function in this device like any other firewall. With NAT we have the possibility to access the internet with a private IP address or to give access from the internet to the services with private IP addresses.
Cisco FTD NAT Applications
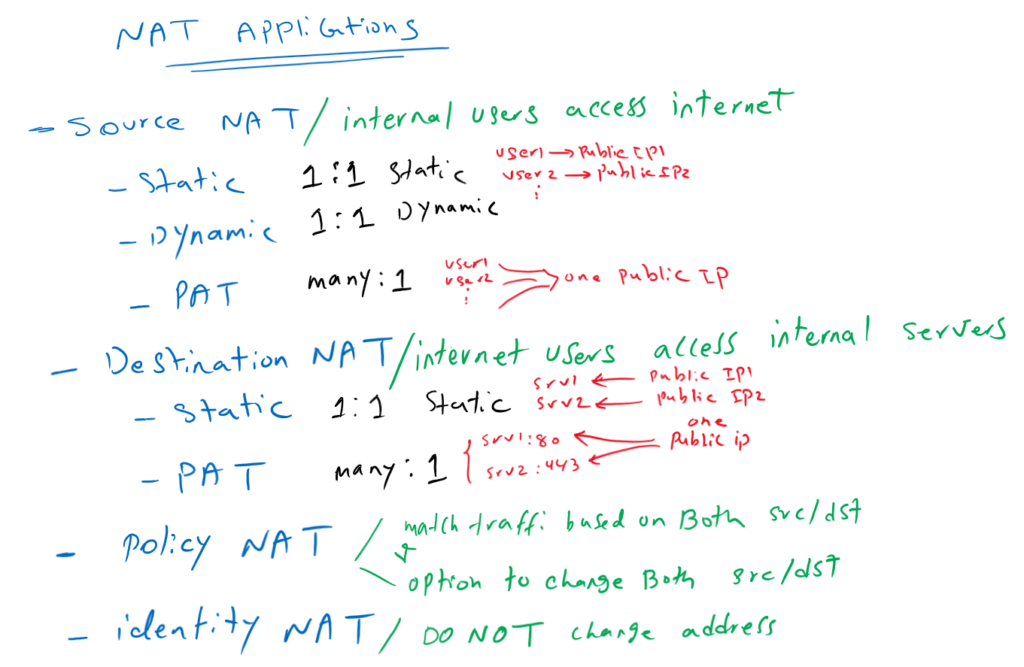
Source NAT and Destination NAT are the most important application of NAT.
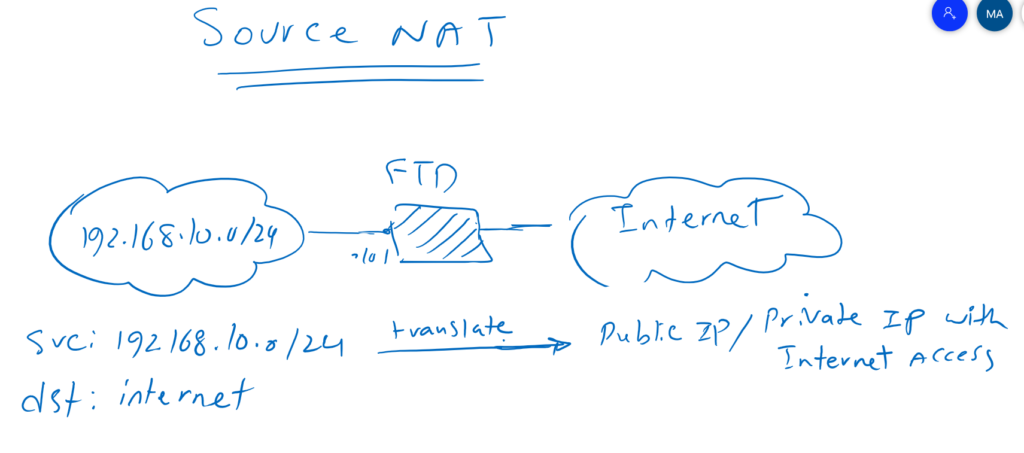
Source NAT
with Source NAT, internal users with private IP address are able to access to the internet. This is possible when the source address is translated to a public IP address.
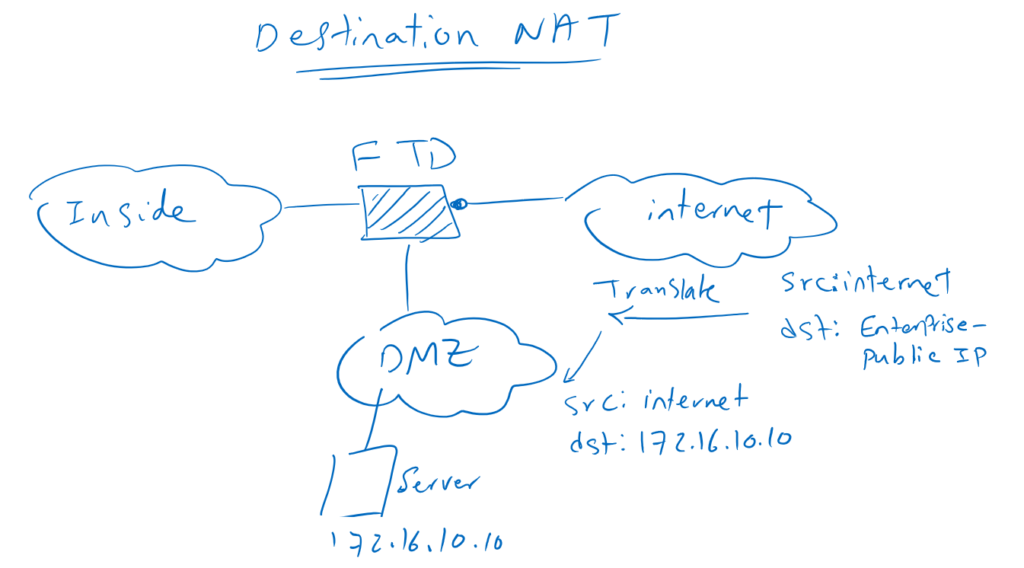
Destination NAT
With Destination NAT, users from the Internet can access the servers with private IP address located in the enterprise. This is possible when destination of internet traffic is translated to private IP address.
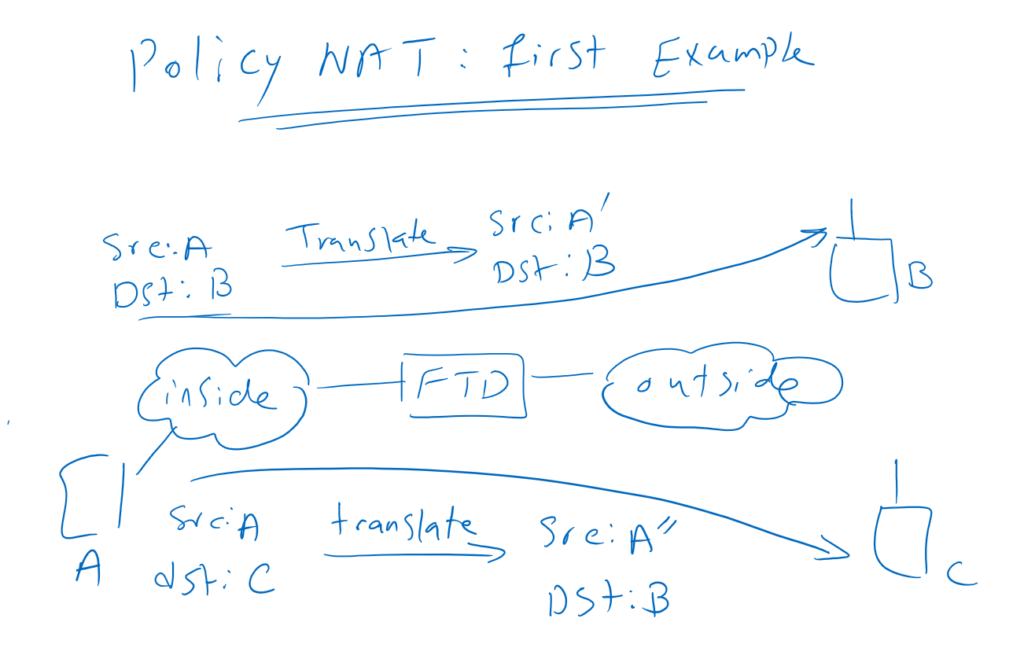
Policy NAT
But sometimes we need more complex NAT scenarios.
As a first example, if source A accesses destination B, we translate source A to A’, but if destination is C, A is translated to A”.
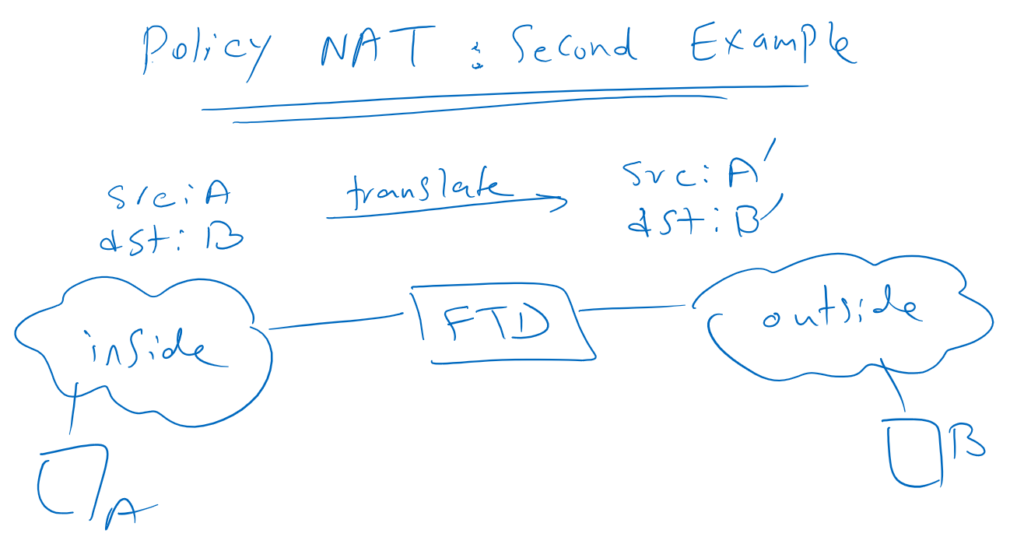
As a second example, if source A accesses destination B, then we want to translate source A to A’ and destination B to B’.
These scenarios are complex NAT scenarios which has normally one or both of these two features:
- We can match both source and destination at the same time.
- we can translate both source and target at the same time.
Notice that Policy NAT are not used only from inside to outside unlike my examples. It can be used between any two zones depending on the application.
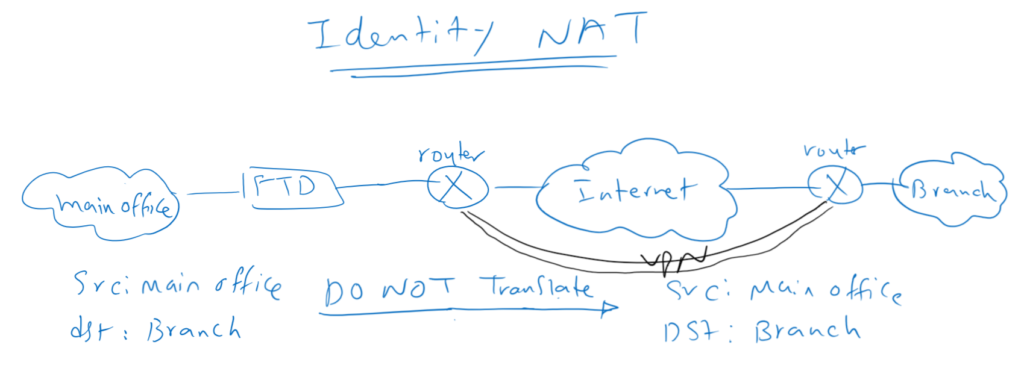
Identity NAT
another application of NAT is “identity NAT” which means “not to translate”. It is mostly used over VPN connections. Traffic with source and destination behind VPN tunnels, do not need to be translated and they can communicate with routing. Also most VPN technologies are not compatible with NAT and it is very important to except VPN traffic from NAT rules.
Static NAT versus Dynamic NAT versus PAT
NAT translations can by static, dynamic or PAT.
Static NAT
With static NAT, there is a one-to-one mapping between original IP address and translated IP addresses. for example user1 is give public IP1 and user2 is given public IP2.
It is less used in Source NAT and is mostly used in Destination NAT. however by default Static NAT is bi-directional. it is activated by default in both directions.
Dynamic NAT
With Dynamic NAT there is also a one-to-one mapping between the original IP address and the translated IP addresses, but this is chosen dynamically from a pool. This method is least used in NAT scenarios.
PAT (Port Address Translation)
With PAT, many private IP addresses use one or a few public IP addresses. It is the most practical method in Source NAT which allows many users inside the network access internet with just a few public IP address.
in our example all users inside the network access the internet with one or a few public IP addresses
Static NAT or PAT in Destination NAT
With Destination NAT, both Static and PAT are useful. With Static NAT, we assign a specific public IP address to each private IP address assigned to the servers.
With PAT, many servers are published on the Internet with only one public IP address. This is possible when services are published on different ports.
as an example, when user from the internet access our single IP address with port 80 then it is redirected to server1 but when user access port 443 with the same public IP address then it is redirected to server2.
How NAT is Implemented in Cisco FTD
The last question is how different type of NAT are implemented in cisco FTD.
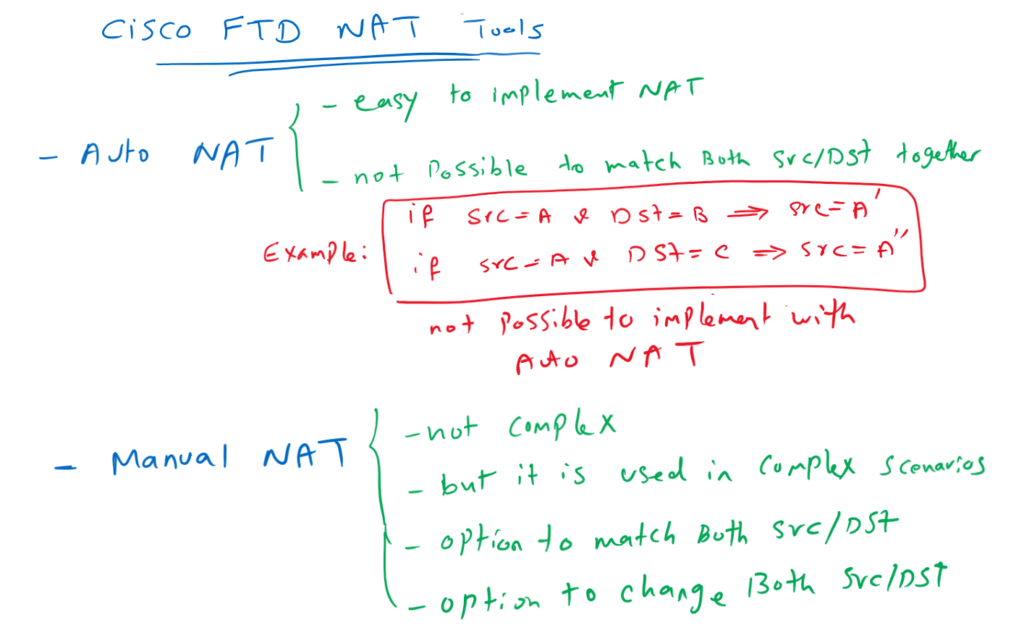
Auto NAT
A simple answer is that source and destination NAT are implemented using Auto-NAT in Cisco FTD. Policy NAT and Identity NAT are implemented using Manual NAT. it is also possible to implement source and destination NAT with Manual NAT. but the reverse is not possible. We can not implement complex NAT scenarios with Auto NAT.
With Auto-NAT, the translation is associated with an object that contains real source addresses or destination addresses, but not both together. Auto NAT can not be used with object group.
Manual NAT
In Manual NAT, you have the option to change or not to change both source and destination address at the same time. in Manual NAT you can call object or object group for both real address and translated address. therefore it is more flexible.
In the next section we start to implement different types of NAT rules.